Targeting and Other Conclusions from a New Month of Third-Party Code
Ty Ehuan, Political Science B.A. & Economics B.S., the university of North Carolina at Chapel Hill
As we approach the end of the year the research team at Duke University and the Media Trust continues to track the presence of malicious activity from third-party code. This blog post aims to update our readers on new trends and conclusions from the data now that we have observed the month of October. Charts visualizing the findings discussed can be found at the bottom of this post. To see previous updates on the status of this project and learn more about the dangers of third-party code please visit our website.
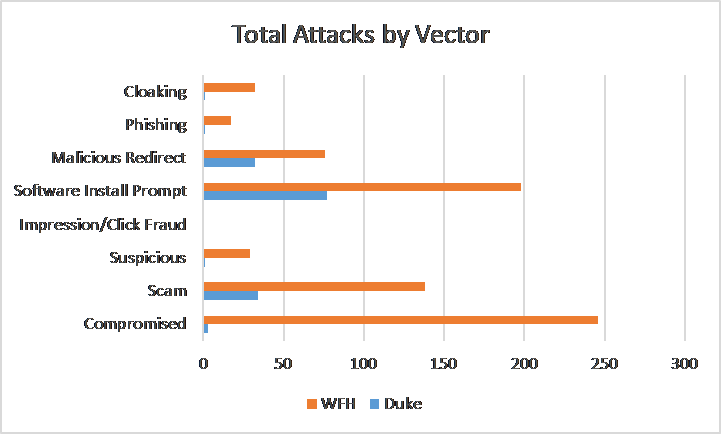
Before we dive into the October data some of the trends observed in the September update are worth revisiting. Compromised Content attacks continued to be a nonfactor for the Duke profiles while remaining a large vector for remote workers. Scan counts have kept declining since we reported it last month, marking the fourth straight month they have gone down. Finally, we have used statistical analysis tools to examine the large difference between the Google Fiber and Spectrum IP’s for remote workers. After adjusting for scan counts and taking the log percentage of attacks to normalize the data we used a two sample t-test to find that there is no significant difference between the amount of attacks faced by the Spectrum IP and the Duke profiles. However, the difference between the Fiber IP and Duke is significant at the 99% level using this same test. This confirms our hypothesis that the difference is occurring on the Fiber IP and emphasizes the need to explore this discrepancy further.
Moving on to the October data, malicious third-party code remained a major issue with .07% and .17% of web interactions with our Duke and Work from Home profiles respectively resulting in these incidents. This represents a slight decline for both profiles but as we previously discussed it still means individuals will encounter malware on the web every day on average.
It is hard to say exactly why malicious actors have decreased their volume this past month. One potential cause may lie in online advertising as the primary source for third-party code. As we move closer to Black Friday and holiday gift shopping season purchasing online advertising becomes more expensive due to higher demand from firms. Thus some bad actors who wish to exploit people’s increased shopping may find it too expensive to take advantage of this opportunity.
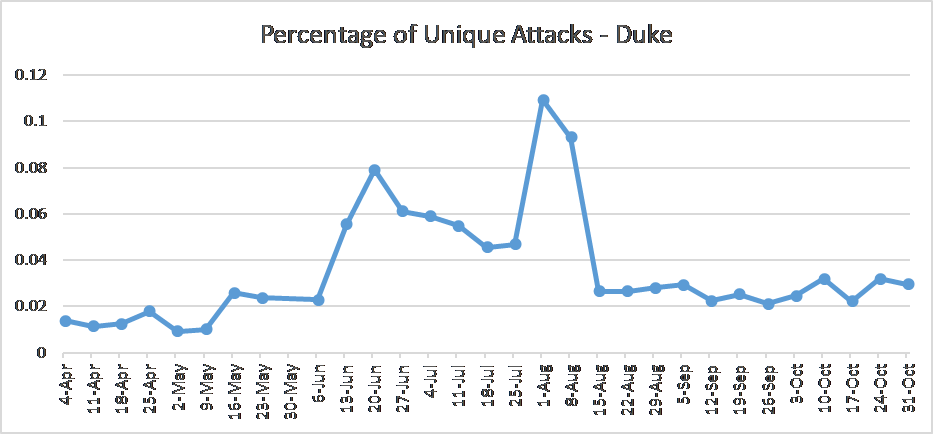
Finally, the growing gap between our Duke and Work from Home profiles deserves examination. There could be many reasons remote workers are the preferred target for malware, but one area of insight lies in the attack pattern. Looking at the weekly breakdown it became apparent that there was a spike in attacks on the Duke profiles from the second week of June to the second week of August, a period that corresponds almost perfectly to the summer months. It may be that when students are at home for the holidays they are more frequently attacked but during the school year they are considered lower value targets. If this is the case, we may see a similar spike at the start of student’s winter break which is something the research team will be watching for going forward.